
Follow Basics and promote 'End Users' as Cyber security warrior
Arvind Kumar, Head IT, Genisys Group | Wednesday, 28 October 2020, 05:58 IST
 Cyber Security or I precisely say "Digital Security" is very critical part for any Organization to protect them from cyber threats / attack or any data loss. I hope everyone will be agree that cyber-attacks has raised their bars in past decade and threaten almost every industry sector.
Cyber Security or I precisely say "Digital Security" is very critical part for any Organization to protect them from cyber threats / attack or any data loss. I hope everyone will be agree that cyber-attacks has raised their bars in past decade and threaten almost every industry sector.
Now we have connected smart devices everywhere like smart phone, smart TV, smart assistance and many more smart sensors for light, water, air etc. after implementation of IoT / IIoT devices in almost every industries vertical. Today, these smart devices or sensors are favourite targets of hackers along with ransomware attacks by which they are not only able to take control of entire business operation or production environment but also able to dilute the business/brand reputation, so it became very critical to secure all connected devices whether it’s a PC, Laptop, smartphone or any smart sensor (Iot / IIoT), not only to safeguard critical business data but also from business operation hijacking.
To make organizations safe / secure from any external threat, it not just only implementation of sophisticated security tools /devices, which can have better control system in place. But also as a proactive action, everyone has to be prepared with very basics i.e. First and foremost have a proper backup solution for all relevant servers, network devices and user data, test them on regular basis by restoring in test environment setup. It is also important to conduct information security awareness programs for all users to let them understand security needs better, on "what to Do and What not?", especially to those user who all are working with IoT or data processing, since Human resource is weakest link in IT / cyber security of an Organization.
Regular / periodic or random IT audits are the key to make sure, all service security processes are in place and adhered by users. If any GAP found after audit analysis, then it can be fixed on immediate basis rather to find & fix it after any accident. This process may provide much more fruitful results if we coupled Red and Blue security teams as part of audit processes.
Most of the organizations implements information security process just for sake of compliance as per government regulation requirements, but does not implement it properly, which leads to become easy target for cyberattacks.
Some of the statics available for cyberattacks and spent on cyber security.
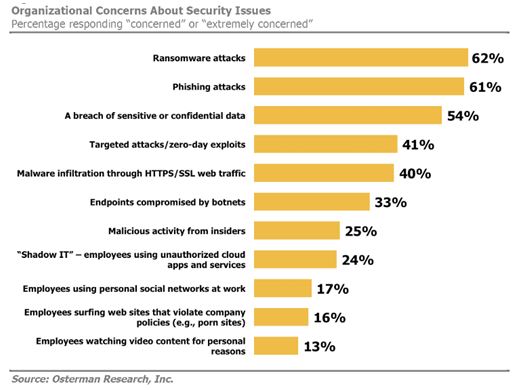
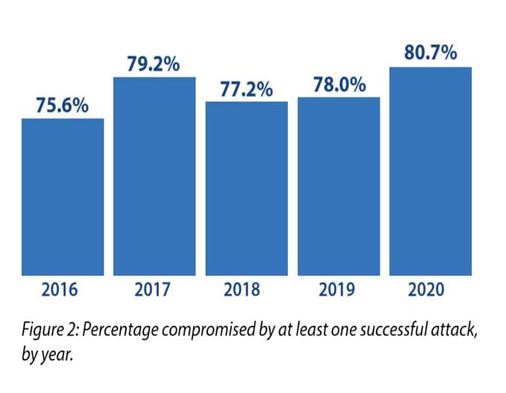
If we see the above trend, it is increasing year by year, since more sophisticated tools and higher computing power is available not to organization but also to hacker.
As per cyberattack trend, you may observe that most attacks are ransomware, phishing, Data Breach and targeted zero day attacks. These attacks are mostly due to end user mistakes either by execution of wrong hyperlink, opening of unknown files or by visiting wrong or look alike websites, which have embedded malware, adware or ransomwares. Organizations invest lots of amount of money on sophisticated tools and security devices but does not invest for end user training on basic information security awareness programs, due to which end user remain the weakest link in organization’s digital or information security framework.
Now organizations must start thinking to invest on their end user training for basic cyber security training programs on regular basis. These training can be conducted by internal IT security team or internal IT security auditor. You may assess user on their knowledge understanding and provide some acknowledgement certificate to encourage them. By this way you not only enhance the information security awareness among your user but also increasing the security layer by many folds. You may randomly take assessment of user knowledge on security information and accordingly plan another round of security awareness training/ program. This investment not only improve your information security but also provide greater ROI by safeguarding data and reducing the chances of getting any malware/ransomware attack unknowingly.
Last few months are really an eye opener for organization, where employees are working from home and there is no perimeter protection available for them to protect from threats available over direct internet access, we also observed few of the organization got hit by some ransomware attacks during this period. If we enable our users / employees as cyber warrior (by investing on information security awareness training program) along with technology then we can make our cyber defence stronger by many folds to protect our organizations and reduce the cyberattack risk by almost 90% of available risk landscape.
I hope Organization will start thinking not only to invest on information security team and security drives but also to train end users as information security warriors.
CIO Viewpoint
From VPNs to Zero Trust: The Transition to a...
By Shankar Venkatesan, Senior IT Leader, Avalon Technologies
The Cyber Security Spar in Integrating IT and...
By Vimal Goel, CIO, HPCL-Mittal Energy
Towards Cyber Resilience: A Data-Centric...
By Puneet Gupta, Vice President & Managing Director, NetApp India/SAARC
CXO Insights
Emerging Trends, Challenges & Future Prospects...
By Sujoy Brahmachari, CIO & CISO, Rosmerta Technologies
Exploring Data-First Security and Automation in...
By Maheswaran S, Country Manager - S.Asia, Varonis Systems
Securing IT-OT Converged Infrastructure




.jpg)
.jpg)
.jpg)







